Cyber threat intelligence is information about a prevailing or evolving cyber threat that can be disseminated by threat intelligence partners to organizations in order to reinforce security against cyber-attack vectors.
Cyber threat intelligence data might take the form of rogue IP addresses, known malware hashes, attachments, and
other core threat identifiers. Such data may also include other critical information about a threat activity, like Indicators of Compromise (IOCs), Indicators of Attack (IOAs), the methods used in the attack, and sometimes the motivation or even ID of the attacker. Through threat intelligence sharing community platforms or tools, it is possible to share cyber threat intelligence between organizations and stop attacks before they occur.
Threat intelligence data is used to learn about an adversary and gain insights into current threats. Threat intelligence can be a valuable tool when it comes to lessons learned in Incident Response (IR) and preventing future attacks. Intelligence is used to learn how threat actors are operating. This is of great value to the cybersecurity domain, because nowadays the threat landscape is so broad and adversaries vary widely, from state-sponsored actors to cybercriminals extorting money from their victims.
The Importance of CTI
Every organization has certain core objectives regardless of their size, business type, or geographical location, such as increasing their income, mitigating risks, dropping expenditures, increasing the number of clients and satisfying employees, conforming to regulations, and so on. However, information security is often overlooked and is frequently not seen as a core objective due to its cost, and as a result, the time spent on security awareness training is minimal. To combat this prevalent outlook, in this section, you are going to learn how cyber threat intelligence can have a positive impact on your organization. The key benefits of threat intelligence are as follows:
• Mitigating risk: Adversaries are constantly discovering new ways to infiltrate organizations. Threat intelligence provides visibility into these existing and emerging security hazards, which will reduce the risk of data loss, prevent or minimize the disruption of business operations, and increase regulatory compliance.
• Stopping financial loss: Security breaches can cost your organization in the form of post-incident remediation and restoration processes as well as in fines, investigations, and lawsuits. Using a threat intelligence tool can help you to make timely, informed decisions to prevent system failure and the theft of confidential data. It also assists in protecting your organization’s intellectual property and in saving your brand’s reputation•
Increasing operating success: Threat intelligence helps in the creation of a more efficient security team. Using automated threat sharing platforms to validate and correlate threat data, and to integrate the data into your organization will strengthen your security posture and can lower your IR time. Moreover, it will allow your operational workforce to work more efficiently and will save your business money.
• Reducing costs: Threat intelligence benefits any kind of organization regardless of its shape and size. It helps process threat data to better understand attackers, respond to incidents, and proactively predict and block the possible next moves of attackers. Leveraging external threat intelligence can reduce costs
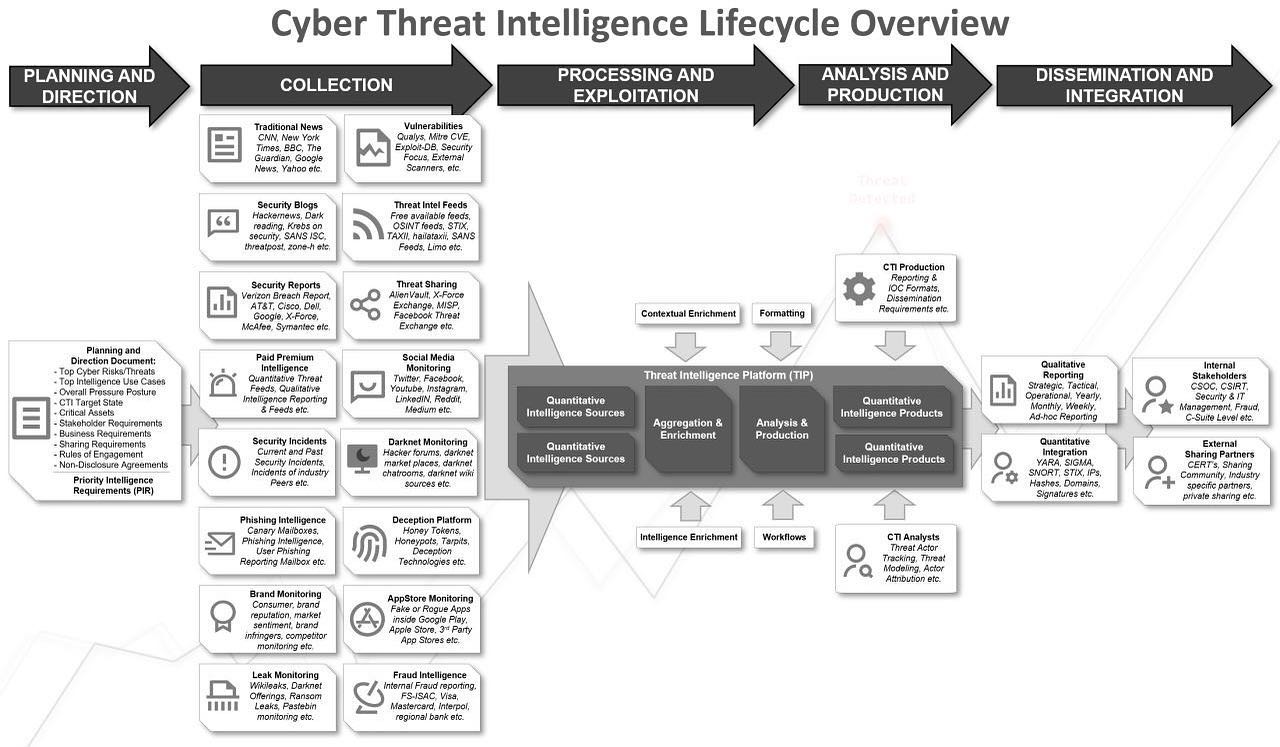
Key pointers when building your CTI Program:
1. Start with a “planning and direction document” to derive the Priority Intelligence Requirements (PIR)
2. If you have limited or non-existent budget start with open source/free first.
3. Be aware that a vendor collection scope might overlap but might vary in terms of quantity or quality.
4. There is no one single vendor that does everything perfectly.
5. SOAR seems one of the best product Categories out there that is able to a lot of the later CTI Lifecycle steps (although only a sub-set of SOAR vendors support TIP-like platform capabilities).