VMware İçin Acil Yama Vakti
VMware, VMware ESXi,VMware Workstation Pro, / Player (Workstation), VMware Fusion Pro / Fusion (Fusion), VMware Cloud Foundation (Cloud Foundation) ürünleri için güncelleme yayınladı. Zafiyet duyurusu kritik olarak nitelendirilirken güncellemelerin vakit kaybetmeden yapılması büyük önem taşıyor.
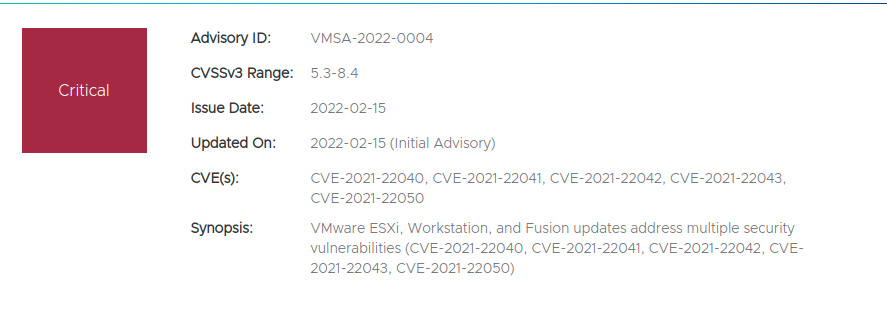
İlk olarak;
3a. Use-after-free vulnerability in XHCI USB controller (CVE-2021-22040) ve 3b. Double-fetch vulnerability in UHCI USB controller (CVE-2021-22041)
Response Matrix: – 3a & 3b
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| ESXi | 7.0 U3 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | ESXi70U3c-19193900 | KB87349 | FAQ |
| ESXi | 7.0 U2 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | ESXi70U2e-19290878 | KB87349 | FAQ |
| ESXi | 7.0 U1 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | ESXi70U1e-19324898 | KB87349 | FAQ |
| ESXi | 6.7 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | [1] ESXi670-202111101-SG | KB87349 | FAQ |
| ESXi | 6.5 | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | ESXi650-202202401-SG | KB87349 | FAQ |
| Fusion | 12.x | OS X | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | 12.2.1 | KB87349 | FAQ |
| Workstation | 16.x | Any | CVE-2021-22040, CVE-2021-22041 | 8.4 | Important | 16.2.1 | KB87349 | FAQ |
Impacted Product Suites that Deploy Response Matrix 3a & 3b Components:
İkinci olarak;
3c. ESXi settingsd unauthorized access vulnerability (CVE-2021-22042) ve 3d. ESXi settingsd TOCTOU vulnerability (CVE-2021-22043)
Response Matrix: – 3c & 3d
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| ESXi | 7.0 U3 | Any | CVE-2021-22042, CVE-2021-22043 | 8.2 | Important | ESXi70U3c-19193900 | None | FAQ |
| ESXi | 7.0 U2 | Any | CVE-2021-22042, CVE-2021-22043 | 8.2 | Important | ESXi70U2e-19290878 | None | FAQ |
| ESXi | 7.0 U1 | Any | CVE-2021-22042, CVE-2021-22043 | 8.2 | Important | ESXi70U1e-19324898 | None | FAQ |
| ESXi | 6.7 | Any | CVE-2021-22042, CVE-2021-22043 | N/A | N/A | Unaffected | N/A | N/A |
| ESXi | 6.5 | Any | CVE-2021-22042, CVE-2021-22043 | N/A | N/A | Unaffected | N/A | N/A |
Impacted Product Suites that Deploy Response Matrix 3c & 3d Components:
Üçüncü olarak;
3e. ESXi slow HTTP POST denial of service vulnerability (CVE-2021-22050)
Response Matrix
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| ESXi | 7.0 | Any | CVE-2021-22050 | 5.3 | Moderate | ESXi70U3c-19193900 | None | FAQ |
| ESXi | 6.7 | Any | CVE-2021-22050 | 5.3 | Moderate | [1] ESXi670-202111101-SG | None | FAQ |
| ESXi | 6.5 | Any | CVE-2021-22050 | 5.3 | Moderate | ESXi650-202110101-SG | None | FAQ |
Impacted Product Suites that Deploy Response Matrix 3e Components:
Kaynak: https://www.vmware.com/security/advisories/VMSA-2022-0004.html









