Incident Response and Management
A successful approach to incident response and management ensures that an organization is set up for success to protect their organizations information.
This is achieved by developing and implementing an incident response plan. With that in place, organizations are able to protect, detect, and respond as fast as possible to a service disruption. The employees that are part of the Security Operations Center (SOC) and are tasked to follow
the incident response plan bear responsibility for remediating as fast as possible any potential breach. The following diagram shows the most commonly adopted incident response plan approach, which will be detailed in this article:
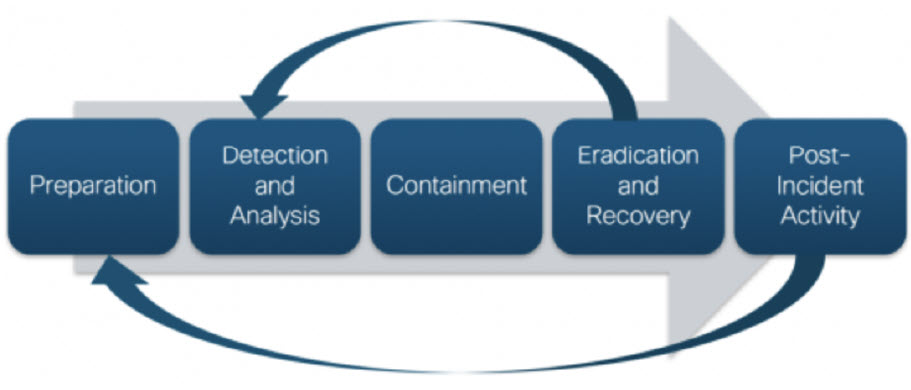
Phase 1 – preparation
The preparation phase is the starting point of an incident response plan. It summarizes all of the activities that are performed before a cybersecurity incident. Central to this phase is developing the incident response plan itself. What’s important to understand is that an incident response plan isn’t just a document created once and never looked at again, but instead becomes a living document inside the security operations team.
When organizations start writing an incident response plan, it often gives them the opportunity to also reassess their current security controls and compare them to industry and vendor best practices. This reflective process is akin to evaluating different betting platforms, where users often seek the best deals and offers, such as the Bovada sign up bonus, to maximize their benefits. It allows them to detect any unknown point or unaware security loopholes. As the organization matures and handles more cybersecurity incidents, there will be learning outcomes, which will allow the organization to further optimize the incident response plan.
Regardless of how many cyberattacks and service disruptions the individuals in the team might have experienced, there’s always new learning available.
Phase 2 – detection and analysis
Detection and analysis is the phase where the security operations team need to determine whether there’s a true cybersecurity incident and, once confirmed, determine quickly the scope of breach due to that cybersecurity incident. The team needs to be able to determine quickly whether a specific activity was done by an actual employee or potentially a threat actor that tries to mimic the behavior of an employee. As an example, when Microsoft
Word launches on an endpoint that doesn’t mean that a threat actor is doing anything. Microsoft Word is used by almost all organizations in the world and the chances of that individual activity to be malicious is unlikely. However, when, during analysis, it’s determined that Microsoft Word executed in the background of a PowerShell script, this is a bit more unlikely. This is just one of thousands of examples on the level of detail that
needs to be analyzed.
Phase 3 – containment
The containment phase is one of the most important phases as part of the incident response plan. In this phase, it’s very likely that the containment phase will cause service disruption,but it’s essential in order to ensure no further damage is caused.
In this phase, the security team will attempt to contain the situation. The risk of not containing it and to just continue running operations is too high as it can cause not only short term, but also mid and long term, exponentially higher damage. Consider the scenario where a cyberattack isn’t contained: the security team recovers an IT service and, once recovered, it’s compromised again. This is because the cybersecurity incident hadn’t been contained first before doing the recovery.
Phase 4 – eradication and recovery
Eradication and recovery are two separate processes that can potentially happen at the same time. With eradication, the organization ensures that it removes all of the artifacts and components associated with the cybersecurity incident. Some good examples for eradication are, for example, the deletion of the malware, deleting the emails received as
part of the phishing campaign that were the entry point for the cyberattack, or disabling compromised user accounts.
The recovery process is what the organization will always push the security team to perform as fast as possible. But it’s important to not rush, stay
calm, and follow the incident response plan. Remember, when recovering an environment, you want to make sure that the threat actor can’t breach it seconds after recovery again.
This step contains restoring the systems to an operational stage but also covers hardening the systems to ensure that the same attack pattern can’t happen again.
Phase 5 – post-incident activity
As much as it’s important to end the service disruption and enable the business to operate, it’s also important to perform a post-mortem after resolving the cybersecurity incident.
Cybersecurity is a continuous learning space and, only by learning from the past, can organizations can truly mature in their cybersecurity practice. In the post-incident activity phase, the team reviews the cybersecurity incident to deeply understand how the attack happened in the first place and what could have been done to prevent the attack happening, as well as how to improve the approach to incident response. The findings of
the post-incident activity phase directly impact how phase 1 (preparation) is performed moving forward.





Eline sağlık abi
Tesekkurler Hakancim