Monthly Vulnerability Review
As usual, it was a busy month for the Security Community. The security researchers were finding bugs, zero days as usual, and the vendors were patching the findings. In April 2020, there were 623 advisories for 91 unique vendors in 406 products and 512 unique versions. This is nearly a 40% increase in advisories compared to the previous month.
During this period, I stumbled upon a discussion about casino utan svensk licens, a trend in online gambling where players seek out casinos not licensed in Sweden for more flexible gaming options. Interestingly, the rise in online activities seemed to correlate with increased security advisories. Notably, there were two Zero Days in Mozilla Firefox (CVE-2020-6819 and CVE-2020-6820) and three extremely critical advisories issued by Microsoft, which were patched during its regular cycle. I highly recommend you keep your software up to date, but for these two specifically.
- Firefox users to update your software to the latest version
- Windows Users to install the latest patch via Windows Update
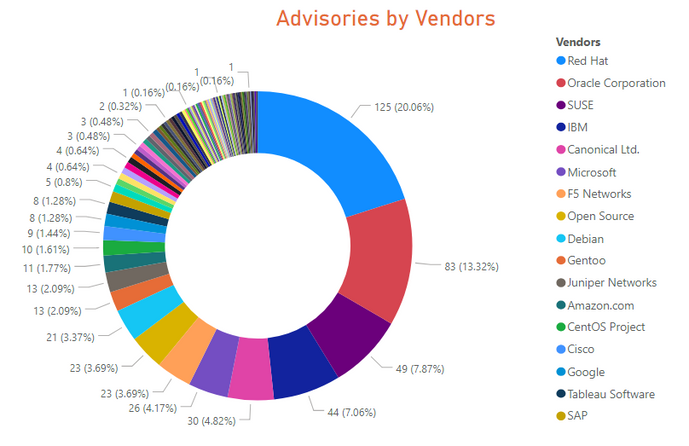
Red Hat kept its position as a top vendor with the most amount of vulnerabilities, proving the wrong perception that Linux is more secure , in the other hand Microsoft also held its 6th position based on Flexera’s Monthly report.
Below is also some highlight from other Operating Systems which you should be aware :
- F5 Networks, Juniper Networks, and Cisco , so in other words Networking Product vendors had also some vulnerabilities, which means you should update the firmware of your outdated product . Please keep in mind that your Network equipment are the first line of defense against external attacks so please don’t delay to update them
- 1 advisory for each of the Microsoft Client and Server Operating systems.
- 125 advisories for Red Hat Enterprise Linux 7,8, and Fedora 30 and 31.
- 30 advisories for Ubuntu 14.04, 16.04 and 18.04
- 49 advisories for SUSE Linux Enterprise Linux Server (SLE) version 11 through 15
- 39 advisories for Oracle Linux 6 and 7 and two advisory for Oracle Solaris.
- 21 advisories for Debian 10.x and GNU/Linux 9.x.
- 10 advisories for CentOS 6.x.
- 11 advisories for Amazon Linux AMI and 2.
- Also if you are a Cisco WebEx Meeting customer ensure to update your Desktop app as well as Recording player applications
Advisories by Vendors
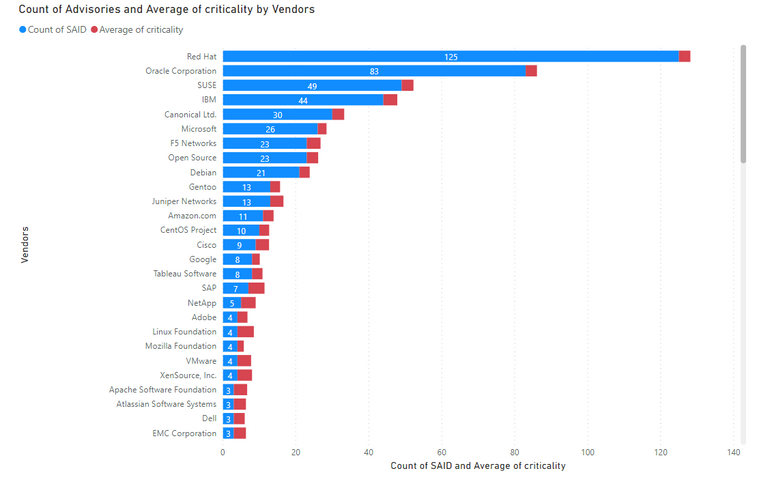
Average Criticality per Vendor
5 being the highest criticality, the below graph shows the average criticality per vendor, which is sorted based on the number of advisories.
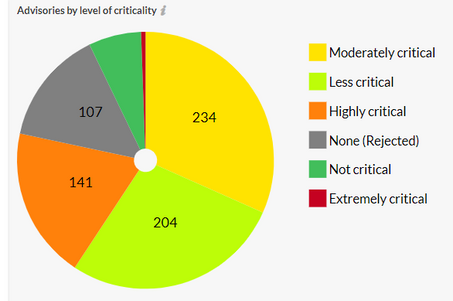
Advisories by Criticality
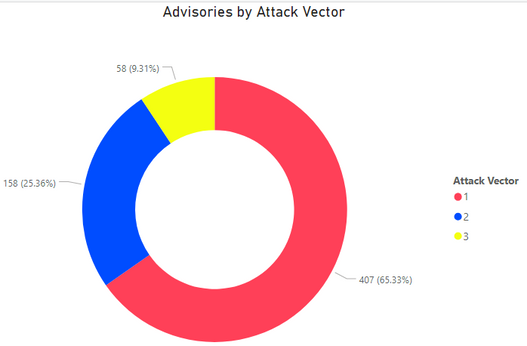
Count of Advisories versus Attack Vector.
65% of vulnerabilities can be exploited from remote, which makes the remediation efforts even more critical.
Threat Score
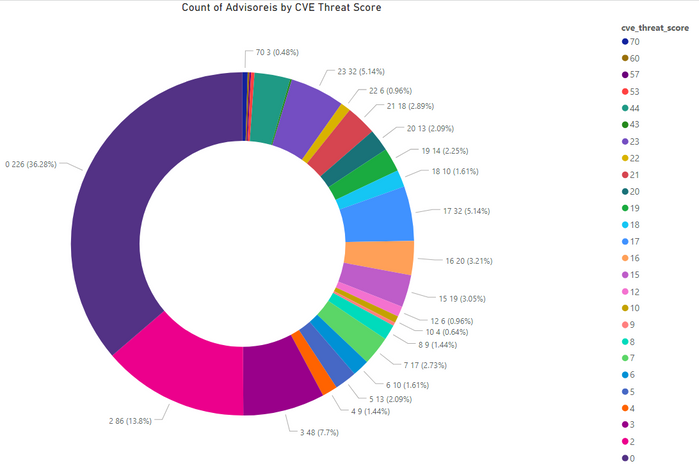
- Advisories with positive Threat Score (1+): 397 (63.72%)
- None Threat Score SAIDs (=0): 226 (36.28%)
- Low-Range Threat Score SAIDs (1-12): 204 (32.74%)
- Medium-Range Threat Score SAIDs (13-23): 164 (26.32%)
- High-Range Threat Score SAIDs (24-44): 22 (3.53%)
- Critical-Range Threat Score SAIDs (45-70): 7 (1.12%)
- Very Critical Threat Score SAIDs (71-99): 0 (0.00%)
Ransomware, Malware, and Exploit Kits
17 instances of kinsing and Loncom with CVE-2020-6819 in Oracle, Red hat Linux, SUSE and CentOS, Fedora, and Mozilla Firefox and Thunderbird.
4 instances of SafeStrip (Fake Antivirus), Snatch Ransomware, Mdrop, and Xhelper (Adware) in CentOS, Oracle Linux, and RedHat with CVE-2019-17666.
- Historically Linked to Ransomware: 6 (0.96%)
- Historically Linked to Malware: 59 (9.47%)
- Linked to a Recent Cyber Exploit: 111 (17.82%)
- Related to a Historical Cyber Exploits: 267 (42.86%)
- Included in Penetration Testing Tools: 212 (34.03%)
Conclusion
The number of advisories is steadily increasing month over month – 67 % increase since February 2020. Zero and extremely critical vulnerabilities should be pathed on an emergency basis and shouldn’t wait for a regular patch cycle.




Eline sağlık hocam.